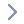Price Oracle Flaw Used to Drain $1.9M From New Gold Protocol, Forensic Report Shows



A newly launched token on BNB Chain, New Gold Protocol (NGP), was exploited just hours after trading went live, with attackers netting roughly $1.9 million in a classic price-inflation attack that relied on manipulating on-chain reserves. Security firm Hacken published a forensic breakdown of the incident this morning, and the on-chain evidence is visible in the transaction and address activity.
According to Hacken’s analysis, the attacker took advantage of the protocol’s price calculation that relied directly on DEX pair reserves, a mechanism that can be trivially manipulated with flash loans. The exploit unfolded in two phases: the attacker first bought NGP tokens in the hours before the main transaction, then used a flash loan to push large USDT→NGP swaps that artificially inflated the token price. With the price pumped, the attacker sold the NGP they had pre-bought and walked away with the proceeds. Hacken says the net haul was about 1.9M USDT.
The on-chain attack transaction (the swap/flash-loan call) is recorded on BscScan and matches Hacken’s timeline and forensic notes. The BSC transaction shows the large PancakeSwap interactions, NGP transfers to the null (dead) address as part of the manipulation, and subsequent movement of proceeds to the attacker’s wallet.
Key Implementation Issue
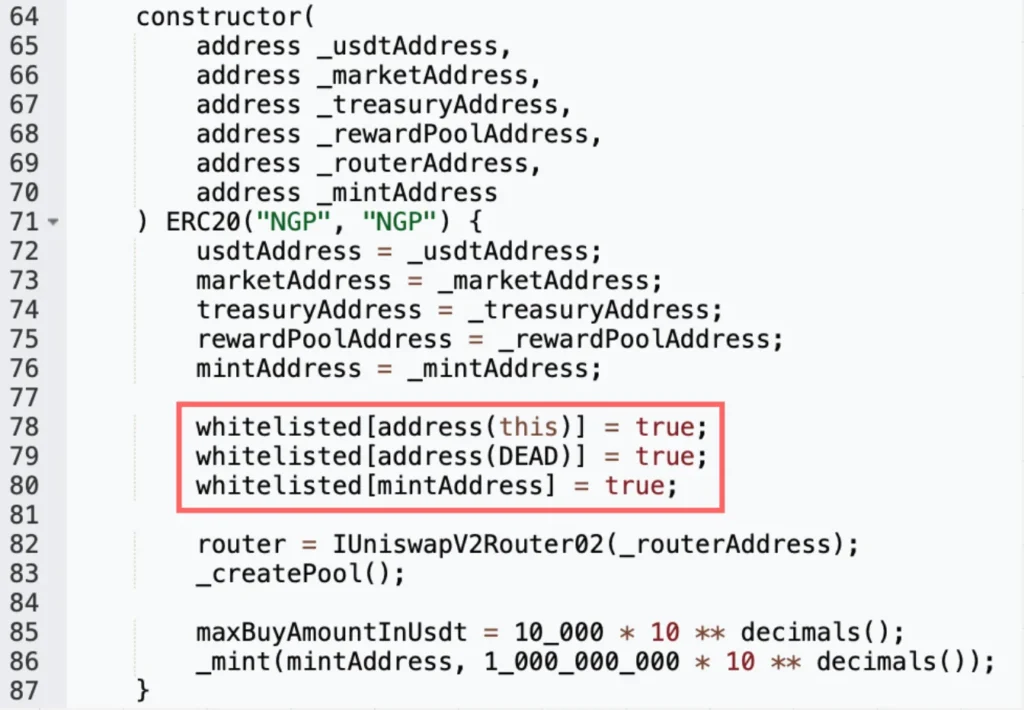
Hacken highlights a key implementation issue that made this possible: the protocol allowed certain addresses (including the token contract, a mint address, and the zero (dead) address) to receive amounts above the per-user buy limit and to bypass cooldowns. The exploiter deliberately used the zero address as the recipient for the flash-loan-driven swaps so the on-chain safety checks wouldn’t trigger, enabling massive USDT→NGP trades that distorted the reserve-based price oracle. After inflating the price, the attacker dumped the tokens they had accumulated earlier and captured the profit.
Once proceeds hit the attacker’s BSC wallet, the funds were quickly converted and laundered: Hacken’s timeline shows the stolen USDT was swapped to Binance-pegged ETH, 443 ETH was bridged to Ethereum via the Across protocol, and much of that was then deposited into Tornado Cash to obfuscate the trail. The attacker’s address and its deposits to Across are visible on BscScan.
The attacker’s BSC address tied to the operation has been identified in the forensic reports and on-chain explorer, investigators and chain-tracking services have already flagged the flows and have been watching the bridging and mixer activity closely.
Security teams and projects launching tokens have long been warned about the dangers of using raw DEX reserves as a price oracle. Hacken’s write-up reiterates several best practices: don’t rely solely on pair reserves for pricing, enforce stronger per-account and per-tx limits, whitelist and tightly control privileged recipients, and run aggressive pre-launch stress tests and independent audits to simulate flash-loan style attacks.
This incident is another reminder that even short windows after a token launch are high-risk moments, and attackers are quick to look for oracle weaknesses and logic that can be bypassed by routing through special addresses. The New Gold Protocol team and affected parties have not publicly released a recovery plan at the time of writing; on-chain evidence and Hacken’s breakdown, however, give a clear picture of how the exploit worked and how future launches might avoid the same fate.

Ethereum Price Prediction, Litecoin Latest News & FTSE100 Updates Here
Ethereum eyes $5,500, Litecoin holds steady near $106, but Remittix steals the spotlight with $26.4M...

What Crypto Presale to Buy Now: Pudgy Pandas, Maxi Doge or BlockchainFX?
BlockchainFX presale surpasses $8M with 10,900+ investors, $0.025 entry price, and BLOCK30 bonus, ti...

Crypto Market Slips as Fear Index Hits 39, $BTC and $ETH Extend Losses
Crypto market cap falls to $3.88T as Fear Index drops to 39, with Bitcoin ($BTC) and Ethereum ($ETH)...